Azure Server-side Disk Encryption
Overview
Azure disk encryption is used to secure data hosted on or access through Azure virtual machines. Azure supports the following disk encryption types:
-
Server-side Managed Disk Encryption
- Platform-managed keys
- Customer-managed keys in customer-controlled hardware
- customer-managed keys
By default, Microsoft-managed keys secure the data stored in a storage account on Azure VM. The customer-managed key provides additional control over the encryption method to the user.
Starting with Avi Vantage release 20.1, the use of the customer-managed key is supported for server-side disk encryption. A RSA key is imported to the Key Vault on Azure, or a new RSA key is generated to use the customer-managed key for the server-side encryption. Azure-managed disks use envelope encryption to encrypt and decrypt the data. It encrypts data using an AES 256-based data encryption key (DEK). DEK is protected using customer keys, which is called key encryption key(KEK).
Configuring Azure Server-side Disk Encryption
Limitations
-
Only softand hard RSA keys of size 2080 are supported. For more information, refer to Azure Key Management Table.
-
All resources related to the customer-managed keys (Azure Key Vaults, disk encryption sets, VMs, disks, and snapshots) must be in the same subscription and region.
-
Disks, snapshots, and images encrypted with customer-managed keys cannot move to another subscription.
Configuring Microsoft Azure
To configure the key vault and Setting up your Azure Key Vault and DiskEncryptionSet, follow the steps from step 1 to 4 of Server-side encryption of Azure Disk Storage.
Configuring Avi Vantage
Using Avi UI
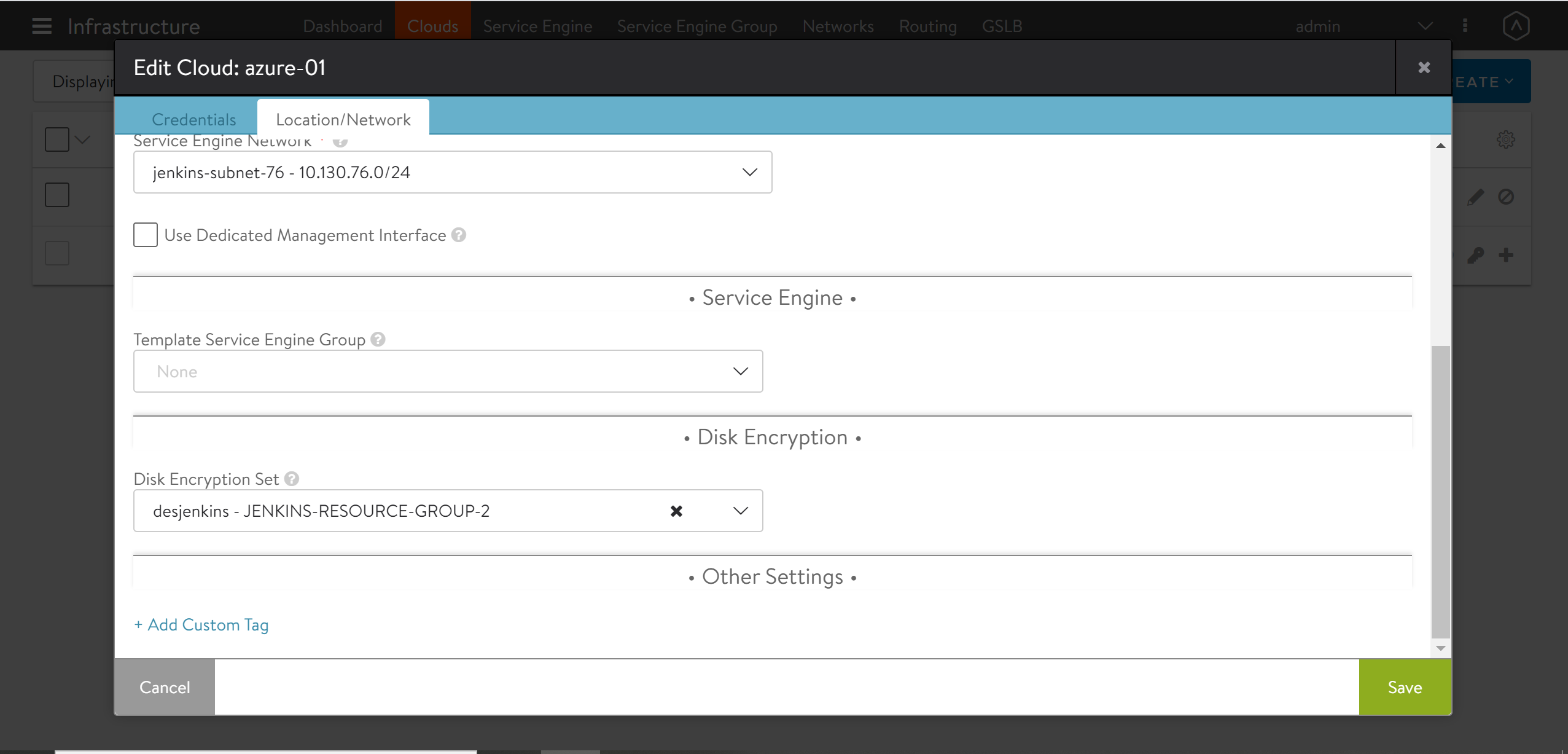
The Disk Encryption Set option is available on Avi UI to select DES ID. Navigate to Infrastructure > Cloud > Location/Network, and use the drop-down list to select the DES ID as shown below.
Using Avi CLI
Server-side managed disk encryption with customer-managed keys allows Avi Controller to create encrypted SE Image and create SEs with encryption on OS and Azure Managed disk only.
Starting with Avi Vantage release 20.1.1, a new field des_id is introduced, which take DES resource ID as input for Azure cloud configuration. Use the following configuration while creating an Azure cloud.
[admin:controller]: > configure cloud Default-Cloud
[admin:controller]: cloud> azure_configuration
[admin:controller]: cloud:azure_configuration> des_id /subscriptions/0eebbbed-14c0-462e-99e0-daaaaaaaaa9/resourceGroups/avi-resource-group/providers/Microsoft.Compute/diskEncryptionSets/DESavi
[admin:controller]: cloud:azure_configuration> save
[admin:controller]: cloud> save
Note:
- SE image and SEs with encrypted OS and Azure Managed disk have the same DES ID.
- Different DES IDs are not supported among SE VMs or Image and SE VMs.