SAML Configuration on Avi Vantage Version Prior to 18.2.3
Overview
This guide explains the process to configure an application for SAML-based authentication, the application needs to be registered at an IDP, such as Okta or PingFederate, with details including the redirect URLs etc. This will yield an IDP metadata XML file that needs to be configured on the SP, in our case, an Avi virtual service.
Notes:
- Ensure that the SSO URL and entity ID match on the IDP and the SP as explained below.
- For configuring SAML for Avi Vantage release 18.2.3 and later versions, refer to to SAML Configuration on Avi Vantage 18.2.3 and Later Versions.
Configuration via Avi UI
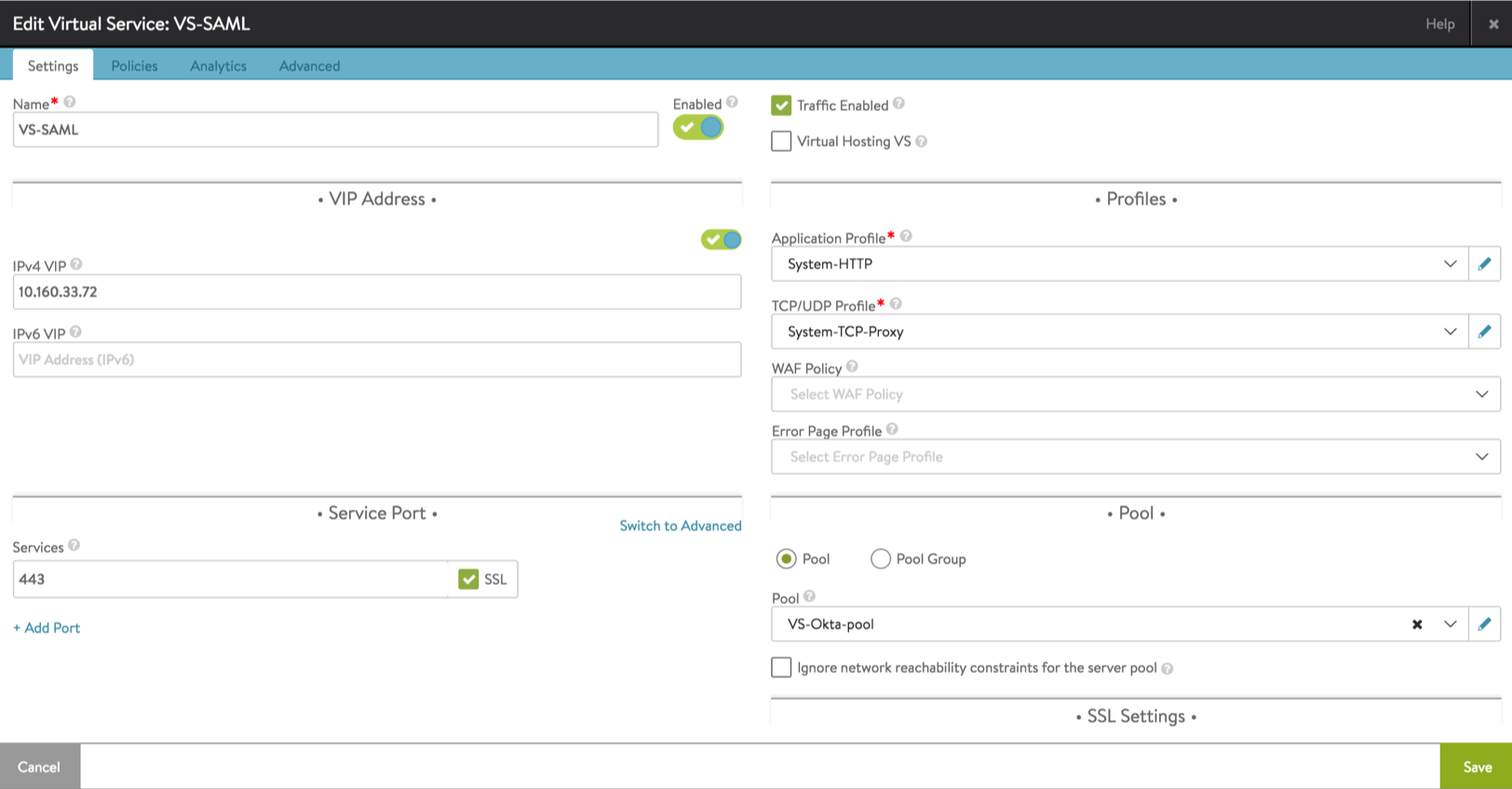
- Create a virtual service to load balance your back-end application. You can follow the instructions given in the Create a Virtual Service article.
- Once the virtual service is configured, go to Templates > Security > Auth Profile.
-
Create a new auth profile. Set the Entity Type to Application VS as shown below.
The following are the Mandatory fields:
- IDP Metadata from the identity provider
The following are the Optional fields:
- Organization Name of the service provider
- Organization Display Name of the service provider
- Organization URL of the service provider
- Technical Contact Name
- Technical Contact Email
Note: By default, Avi Vantage does not sign the SAML authentication request. However, this behavior can be altered by adding an SSL certificate to the auth profile. Bind a certificate to the auth profile, and the Avi VS will start signing authentication requests using that information.
- Click on Save.
-
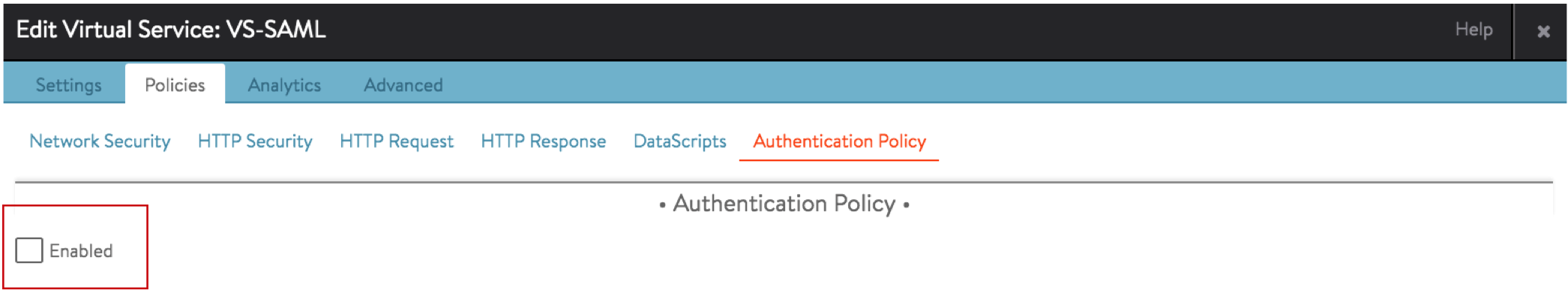
Go to the virtual service created in step 1 and click on Policies.
-
Go to Authentication Policy and check Enabled box.
-
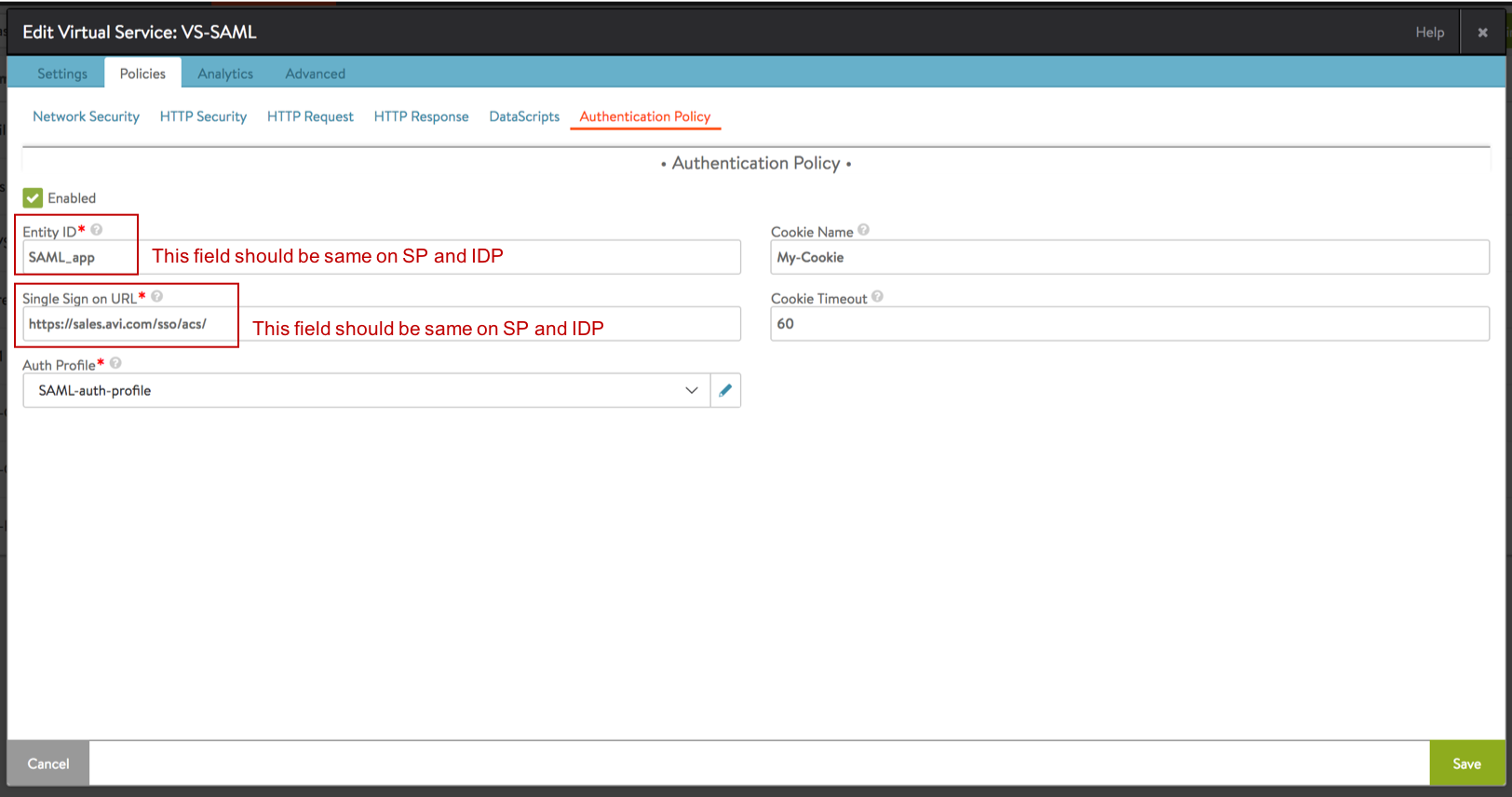
Configure the fields and chose the auth profile created above.
- Entity ID: A unique value that should be same on both the IDP and the SP.
- Single Sign-on URL:
https://SPresource/sso/acs/. This same URL needs to be programmed into the IDP as well.
Example —https://sales.avi.com/sso/acs/
Note: The trailing slash afteracsis mandatory. - Cookie Name: Avi Vantage validates the assertion and sets a cookie for the client. The client sends a «code>GET</code> request to access the resource with the cookie that the SP provided. The cookie name is configurable and be specified via this field. If no name is specified, the Avi VS uses a randomly generated name for the cookie, such as
XRWDFG. -
Cookie Timeout: The cookie expiry time can be customized here. The default value is 60 minutes.
Click on Save.
Configuration via Avi CLI
Login to the Avi shell.
Configuring the Auth Profile
In place of the last line in the following command-line sequence, insert metadata as illustrated in the example.
[admin:ctrlr-1]: > configure authprofile SAML-auth-profile
[admin:ctrlr-1]: authprofile> type auth_profile_saml
[admin:ctrlr-1]: authprofile> saml
[admin:ctrlr-1]: authprofile:saml> sp
[admin:ctrlr-1]: authprofile:saml:sp> saml_entity_type auth_saml_app_vs
[admin:ctrlr-1]: authprofile:saml:sp> save
[admin:ctrlr-1]: authprofile:saml> save
[admin:ctrlr-1]: authprofile> saml
[admin:ctrlr-1]: authprofile:saml> new idp
metadata : ‘metadata_string’Example
metadata: ‘<?xml version="1.0" encoding="UTF-8"?><md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="http://www.okta.com/exk2c02xxTcM9pIr0355"><md:IDPSSODescriptor WantAuthnRequestsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"><md:KeyDescriptor use="signing"><ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:X509Data><ds:X509Certificate>MIIDtjCCAp6gAwIBAgIGAWPuJWSOMA0GCSqGSIb3DQEBCwUAMIGbMQswCQYDVQQGEwJVUzETMBEG
A1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5jaXNjbzENMAsGA1UECgwET2t0YTEU
MBIGA1UECwwLU1NPUHJvdmlkZXIxHDAaBgNVBAMME2F2aW5ldHdvcmtzLWF1dGhsYWIxHDAaBgkq
hkiG9w0BCQEWDWluZm9Ab2t0YS5jb20wHhcNMTgwNjExMDkxOTE4WhcNMjgwNjExMDkyMDE3WjCB
mzELMAkGA1UEBhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcMDVNhbiBGcmFuY2lz
Y28xDTALBgNVBAoMBE9rdGExFDASBgNVBAsMC1NTT1Byb3ZpZGVyMRwwGgYDVQQDDBNhdmluZXR3
b3Jrcy1hdXRobGFiMRwwGgYJKoZIhvcNAQkBFg1pbmZvQG9rdGEuY29tMIIBIjANBgkqhkiG9w0B
AQEFAAOCAQ8AMIIBCgKCAQEAiFKBy70aa5G2I5JH+uUqXef9jrhUtx6CX1nmrg26FXtsKYdjRm5v
otxbjfNdcXeXRXHu5scMwAgMy9EZM+AXehlm/qnahNWvEZ+YgPZS55UzkcSXJ30dl62kbUAyXxo3
CQQs+Hj5k7W0rcZAj405qxOZVgtkrs6cB3uS/pn02eV4EHA6ECReQLrEPFcy6zLZpIChbkzyz372
ZLbwMCSjF5DLh52MSGgWixwvs5Mq20WofBWMOnS0ofnZq6+TM6XK7P8VEQxJe37sWi0W+RrR6685
T+bnlM6GMg24wRHt/1fouUbZQuBgoc0/HNKywlO9BXLoJ9j02/VYn3Uex9bumQIDAQABMA0GCSqG
SIb3DQEBCwUAA4IBAQAmAh0fXL7gU1ivV3hWdl0AlLPENREAzKbHwuthtTySBr6rmreo6j8SvOMW
pKQzNznmzU3zyeLd96j6lfA7PIDGyBGmNB6z0Va0bPvOQe+a2f3/cmumVdrKFv7I5ZiR0UNbeBmG
BIeWkJ+Rx+FcaIzP2IiFddmvpdh1nLae7FS9F1jvnioSIwq2PlFZuMMFb2TrMXrqqEMp9CeGfEag
bjxQcWEW1ifNxeKrI/LcS5g5mTf4gx41bgo/w9x6MRsK+bIbYv680mdtb6LhWiT1lZU+ZAYJTKMr
HHoIxYFPW8Zcs7DGirOOYMbSU97G0rljQzbv9gcS+FhwPffBaHi3spk9</ds:X509Certificate></ds:X509Data></ds:KeyInfo></md:KeyDescriptor><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat><md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://avinetworks-authlab.okta.com/app/avinetworksorg108212_apmssotest_1/exk2c02xxTcM9pIr0355/sso/saml"/><md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://avinetworks-authlab.okta.com/app/avinetworksorg108212_apmssotest_1/exk2c02xxTcM9pIr0355/sso/saml"/></md:IDPSSODescriptor></md:EntityDescriptor>’Complete the CLI sequence with two save commands.
[admin:ctrlr-1: authprofile:saml> save
[admin:ctrlr-1]: authprofile> save
Configuring the Virtual Service
[admin:ctrlr-1]: > configure virtualservice VS-SAML (setting for VS which is already up)
[admin:ctrlr-1]: virtualservice> sso_policy
[admin:ctrlr-1]: virtualservice:sso_policy> authentication_policy
[admin:ctrlr-1]: virtualservice:sso_policy:authentication_policy> auth_profile_ref SAML-auth-profile
[admin:ctrlr-1]: virtualservice:sso_policy:authentication_policy> single_signon_url https://sales.avi.com/sso/acs/
[admin:ctrlr-1]: virtualservice:sso_policy:authentication_policy> entity_id SAML_app
[admin:ctrlr-1]: virtualservice:sso_policy:authentication_policy> save
[admin:ctrlr-1]: virtualservice:sso_policy> save
[admin:ctrlr-1]: virtualservice> save