SAML Authentication Policies
Overview
SAML authentication policies is configured as a part of the client authentication implementation. The authentication policy is a combination of rules that are to be matched and their corresponding actions. The rules can be configured to match for client IP, host header, or path match.
The following section discusses configuring authentication policy with corresponding rules and action.
Configuring Auth Policy Using the Avi UI
To configure the authentication policy using the Avi UI,
-
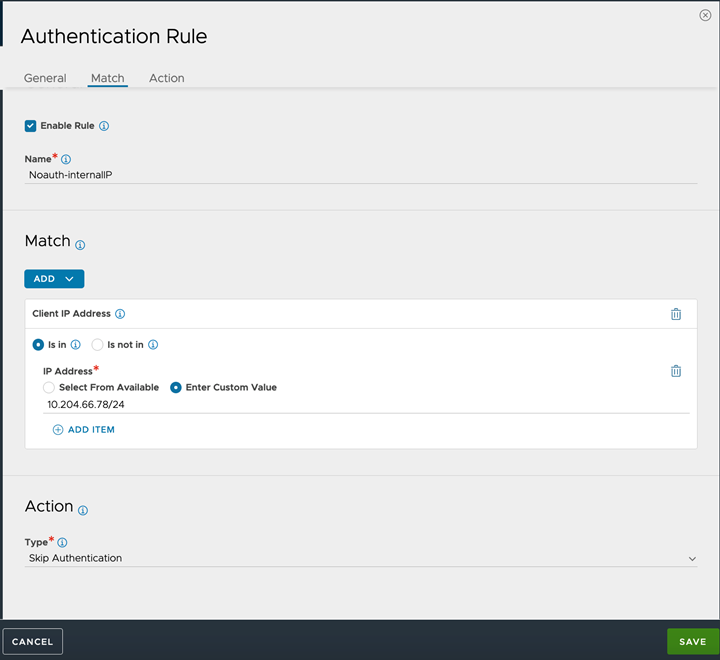
Navigate to Templates > Security > SSO Policy. Note: Alternatively, you can navigate to the virtual service where SSO Policy is bound. From the Edit Virtual Service screen, go to Policies > Access > SAML, select the **SSO Policy attached to the virtual service. Click the pen icon to edit the SSO Policy.
-
Go to Authentication > Authentication Rules.
-
Click Add.
-
In the Authentication Rule screen, enter Name of the Rule.
-
Ensure the option Enable Rule is selected.
-
Add a match condition and action, as required.
-
Click Save.
-
Click Save.
CLI Configuration
The following are the steps to configure authentication policy:
-
Edit the configured SSO policy or create a new SSO policy
-
Create the authentication rules and specify the match condition
-
Define the action for the rules configured
Configuring Authentication Policy and Binding Authentication Profile
To configure SAML authentication policy on Avi Vantage follow the steps below:
Editing the configured SSO policy or create a new SSO policy
To configure SAML authentication policy on Avi Vantage using CLI, follow the steps below:
[admin:controller]: > configure ssopolicy auth-policy-testSAML-SSOpolicy
[admin:controller]: ssopolicy>
authentication_policy (submode)
Creating Authentication Rules
Configure the authentication rules using the authn_rules command.
[admin:controller]: ssopolicy:authentication_policy> authn_rules name rule_1
New object being created
[admin:controller]: ssopolicy:authentication_policy:authn_rules> index 1
[admin:controller]: ssopolicy:authentication_policy:authn_rules> match
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match>
client_ip (submode)
host_hdr (submode)
path (submode) As shown above, the rules can be configured based on three parameters, namely, client IP , host header and path. These are explained in detail as follows:
Client IP
The client IP address of incoming requests will be matched with the rules configured. If a match is found for the client IP, the corresponding rule gets executed:
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match>
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match> client_ip
The client IP match can be the client IP address, address range, IP prefixes, or an IP group.
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:client_ip>
addrs IP address(es)
group_refs name of IP address group(s)
match_criteria Criterion to use for IP address matching the HTTP request
prefixes IP address prefix(es)
ranges (submode)
save Save and exit the current submode
Example: The following code snippet displays configuring a match for client IP address 1.1.1.1.
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:client_ip> addrs 1.1.1.1
addrs IP address(es)
group_refs name of IP address group(s)
match_criteria Criterion to use for IP address matching the HTTP request
prefixes IP address prefix(es)
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:client_ip> addrs 1.1.1.1 group_refs Internal
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:client_ip> match_criteria
is_in is in the configured value(s)
is_not_in is not in the configured value(s)
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:client_ip> match_criteria is_in
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:client_ip> Note: Client IP is subject to the option Use_True_Client_IP. Client IP might be equal to source IP from layer-3 header or equal to the fetched IP from user-defined HTTP header. For more information refer to True Client IP in L7 Security Features.
Host Header
The host header is matched from the configured list of the host header values. Host header can be configured to be case sensitive aware.
The following code snippet displays configuring a match for host header:
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match>
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match> host_hdr match_criteria hdr_
hdr_begins_with header value begins with the configure value(s)
hdr_contains header value contains configured value(s)
hdr_does_not_begin_with header value does not begins with the configure value(s)
hdr_does_not_contain header value does not contains configured value(s)
hdr_does_not_end_with header value does not ends with the configured value(s)
hdr_does_not_equal header value does not equals the configured value(s)
hdr_does_not_exist header does not exist in the HTTP request
hdr_ends_with header value ends with the configured value(s)
hdr_equals header value equals the configured value(s)
hdr_exists header exists in the HTTP request
Example:
The following code snippet displays configuring a match for host header that begins with test.auth.com.
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match> host_hdr match_criteria hdr_begins_with
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:host_hdr> value test.auth.com
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:host_hdr> save Path Match
The path match is matched based on the string group or list of the string values of the path. The path match can be configured to be case sensitive aware.
The following code snippet displays configuring a path match that begins with a string group reference configured for string match/avinetworks.
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match>
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match> path
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:path>
match_case Case sensitivity to use for the matching
match_criteria Criterion to use for matching the path in the HTTP request URI.
match_str String values
string_group_refs name of the string group(s)
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:path> match_criteria
begins_with begins with the configured value(s)
contains contains the configured value(s)
does_not_begin_with does not begin with the configured value(s)
does_not_contain does not contain the configured value(s)
does_not_end_with does not end with the configured value(s)
does_not_equal does not equal the configured value(s)
ends_with ends with the configured value(s)
equals equals the configured value(s)
regex_does_not_match regex pattern does not match with the configured value(s)
regex_match regex pattern matches with the configured value(s)
Example: The following code snippet displays configuring a path match that begins with a string group reference configured for string match/index.html.
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:path> string_group_refs System-Cacheable-Resource-Types
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:path> match_str /avinetworks match_str /index.html
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:path> match_criteria begins_with
[admin:controller]: ssopolicy:authentication_policy:authn_rules:match:path> save Define the Action for the Rules Configured
Currently the following two actions are supported:
-
Skip authentication - To skip authentication if any one of the rules is matched
-
Use default authentication - To use SAML authentication if any one of the rules is matched
[admin:controller]: ssopolicy:authentication_policy:authn_rules> action [admin:controller]: ssopolicy:authentication_policy:authn_rules:action> type skip_authentication Skip Authentication use_default_authentication Use Default AuthenticationTo configure the action as skip authentication, following command can be used:
[admin:controller]: ssopolicy:authentication_policy:authn_rules:action> type skip_authentication [admin:controller]: ssopolicy:authentication_policy:authn_rules:action> save
To view the statistics for the rules executed, use the show virtualservice virtual_service ssopolicy stats and show virtualservice virtual_service internal commands.
Configuring Multiple Indexed Authentication Rules
You can configure multiple indexed authentication rules under each policy. The rules are evaluated in the following order:
-
Index Numbering. The rules are evaluated in the order of the index of the rules, i.e., the rule with index number 1 will be evaluated before the rule with index number 2.
-
The action corresponding to the first rule that is matched is performed and the rest of the rules will be skipped.
-
If no rule is matched, then by default authentication wil be performed.
Each rule is a combination of a parameter match and an action. The parameter can be a client IP (client_ip), host header (host_hdr), or a path match (path).
Note: Host header and path can be configured to be case sensitive aware.