DDoS Definition
DDoS stands for Distributed Denial of Service, a malicious attempt by an attacker to disallow legitimate users access to a server or network resource by overloading it with artificial traffic.
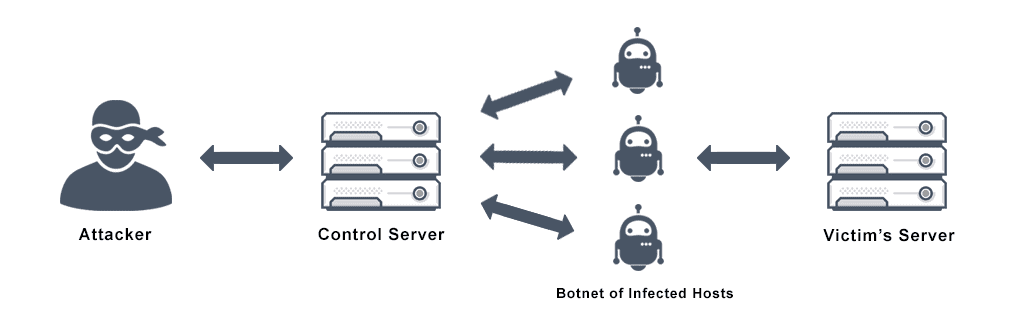
What is DDoS?
Distributed Denial of Service (DDoS) is the effect of a cyber attack in which a server or network resource becomes unavailable for legitimate user traffic. Denial of service occurs as the result of the attack – intentional disruptions of a target host connected to the internet by a perpetrator (attacker).
What is a DDoS Attack and How Does it Work?
DDoS is a type of denial of service (DoS) attack where a perpetrator maliciously attempts to disrupt the normal traffic of a target network or server by flooding the surrounding infrastructure with Internet traffic. This typically involves co-opting large numbers of client devices with a Trojan virus and coordinating them to make requests to the same resource at the same time. Popular for hackers due to its simplicity, DDoS attacks can also be affordable if not profitable, leading malicious actors or “hacktivists” to turn to this form of cyber attack.
In general, a DDoS attack maliciously floods an IP address with thousands of messages through the use of distributed (control) servers and botnets. Victims of an attack are unable to access systems or network resources to make legitimate requests because of unwanted traffic draining the network’s performance.
Types of DDoS Attacks
Types of DDoS attacks range from those that crash services and those that flood services. The three basic categories of DDoS attacks today are volume-based attacks focused on network bandwidth, protocol attacks focused on server resources, and application attacks focused on web applications. Some of the most common DDoS tools include:
• SYN Flood – a Synchronized (SYN) Flood exploits weaknesses in the TCP connection sequence, also known as a three-way handshake.
• HTTP Flood – sends artificial GET or POST requests to use maximum server resources.
• UDP Flood – a User Datagram Protocol (UDP) attack targets random ports on a computer or network with UDP packets.
• Smurf Attack – this type of attack exploits IP and Internet Control Message Protocol (ICMP) with a malware program called smurf.
• Fraggle Attack – similar to a smurf attack, a fraggle attack applies large amounts of UDP traffic to a router’s broadcast network using UDP rather than ICMP.
• Shrew Attack – targets TCP using short synchronized bursts of traffic on the same link.
• Ping of Death – manipulates IP by sending malicious pings to a system.
• Slowloris – uses minimal resources during an attack, targeting web servers in a similar approach to HTTP flooding while keeping connection with target open for as long as possible.
• Application Layer Attacks – go after specific weaknesses in applications as opposed to an entire server.
• NTP Amplification – exploits Network Time Protocol (NTP) servers with an amplified reflection attack.
How to Stop a DDoS Attack
It is important to establish the best DDoS protection for your business to prevent DDoS attacks that could compromise your company data and intellectual property. DDoS protection, otherwise known as DDoS mitigation, is crucial for companies to maintain as DDoS threats are growing. The average week-long DDoS attack costs less than $200, and more than 2,000 of them occur worldwide every day. Firms often pay a fraction of the cost for anti DDoS prevention services compared to the damages that victims of an attack incur.
If you don’t currently have a plan for DDoS attack mitigation, now is a good time to start. DDoS security comes in several different approaches, such as DIY solutions, on-premises tools, and cloud-based solutions.
DIY DDoS Protection
This method is by far the least expensive, but is often considered a weak approach and inadequate for online businesses with decent traffic. The main goal of most DIY defenses is to stop flood attacks by implementing traffic thresholds and IP denylisting rules.
These anti DDoS setups are reactive in nature, usually kicking in after an initial attack. Although this approach might hinder future attacks, most aggressors are able to adapt and modify their methods. Moreover, constraints in network bandwidth with DIY solutions commonly prove ineffective as companies lack the scalability to defend from attack.
On-Premises DDoS Protection
This approach adds an extra layer of hardware appliances deployed on-site at customer data centers along with other networking equipment and servers. On-premises protection can often be an expensive option for DDoS security.
Advantages of the advanced traffic filtering offered by on-premises DDoS protection solutions include low latency, control of data, and compliance with strict regulations in certain industries. Drawbacks involve higher costs for DDoS mitigation, requirement for manual deployment in case of an attack, and constraints on available bandwidth.
Cloud Server DDoS Protection
Off-premise cloud solutions are outsourced services that require less investment in management or upkeep than other DDoS mitigation services, while providing effective protection against both network and application layer threats. These services are deployed either as an always-on or on-demand service and can elastically scale up resources to counteract DDoS attacks. Services such as a Content Delivery Network (CDN) can route traffic filter traffic, offloading malicious requests and sending only traffic determined to be “safe” to the website.
Always-on services enable DNS server redirection, focusing on mitigation of application layer attacks that exhaust server resources. The on-demand option mitigates network layer attacks that target core components of network infrastructure, such as a UDP flood, through elastic scale-up of services.
DoS vs DDoS
A DoS attack is a denial of service attack where one or more computers are used to flood a server with TCP and UDP packets in order to overload a target server’s capacity and make it unavailable for normal users. A DDoS attack is one of the most common types of DoS attack, using multiple distributed devices to target a single system. This type of attack is often more effective than other types of DoS attacks because there are more resources the attacker can leverage, making recovery increasingly complicated.
Does Avi offer DDoS Protection?
The VMware NSX Advanced Load Balancer by Avi Networks protects and mitigates against DDoS attacks by identifying threats, informing admins and automatically protecting against these attacks. Some of the features that are used to accomplish this are TCP SYN Flooding Protection, HTTP DDoS Protection, URL filtering, Connection Rate Limiting per Client, Connection Rate Limiting per User Defined Clients, Limiting Max Throughput per VS, Limiting Max Concurrent Connections per VS and Limiting Max Concurrent Connections per Server.
In addition, Avi’s elastic application services enable on-demand autoscaling of services during an attack giving administrators much needed time to work on mitigating the attack while maintaining quality of service. Learn about the autoscaling of Avi’s Software Load Balancer.
For more on the actual implementation of load balancing, security applications and web application firewalls check out our Application Delivery How-To Videos.